27 Feb 2018
Steal Funds from TenX Users – Just Another Bug Bounty Story
TL;DR
Attention – spoiler alert!
I was able to bypass the rate-limiting protection of the login system of TenX which allowed me to potentially take over every TenX account (with the knowledge of the victims e-mail address) within 30 minutes.
After taking over the account, missing verification functions allow an attacker to change the e-mail address, (this is still the case at the time of writing) as well as the phone-number (via the web app) of the account.
Further, missing additional verification steps allow an attacker to withdraw all funds of the affected account.
TenX ?
TenX is a company based in Singapore, which offers crypto-debit cards and cryptocurrency wallets. In 2017 they collected over 80 Million Dollars via one of the biggest ICOs ever held.
TenX encourages security researchers to submit vulnerabilities via their responsible disclosure bug bounty program which can be found here .
Remote Account Takeover Vulnerability
By the end of November 2017 I had a look at their website and signed up for their service. They require the user to provide an e-mail address as well as a phone number. I was surprised, that no password needs to be defined during the registration - they only offer authentication via one time codes.
NOTE: TenX now supports user defined passwords!
Those codes are sent to the user via SMS or e-mail.
The one time verification code is a 6 digit number which seems to be valid for about 30 minutes.
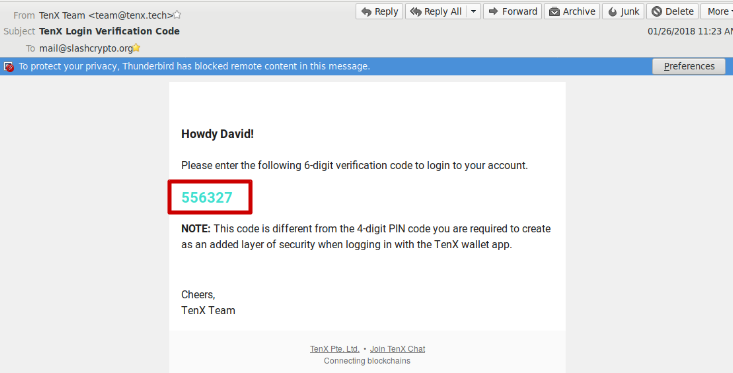
The following screenshot shows an example of verification code which was sent to me via e-mail:
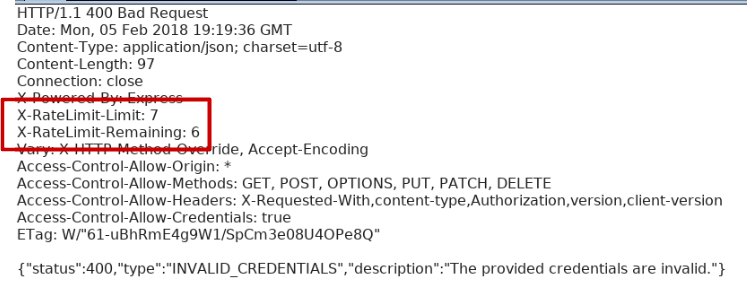
The following screenshot shows the API request which is used to check if a correct code was entered on the web application:
The following screenshot shows the response to the request above:
After checking out the screenshots from above, can you see where this is going to? Yes?
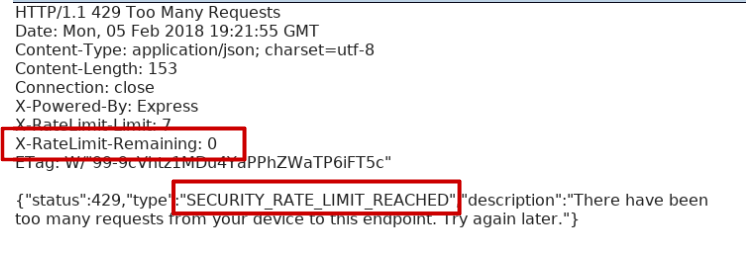
Alright, so we have a rate-limiting which is a really good idea if the only thing an attacker needs to Pwn your account is a 6 digit code …
After submitting the request several times (7 times to be exact), the server said STOP!
Seems to work, right? But I did not stop at this point.
The first thing I tried was to change my source IP address. I used a VPN connection and resubmitted the request from above. I was surprised that the request went through – and the “X-RateLimit-Remaining” response header was set back to 6.
I was able bypass the rate limiting protection by changing my source IP. Lets do some math:
There are 1.000.000 different variations of the one time password; lets assume we find the correct one after 500.000 tries.
500.000 / 6 tries per IP = 83.333 IPs => no practical attack because I don’t have a botnet or anything else which I could use :( .
I continued and started to play around with different Request-Headers. The “X-Forwarded-For” Header is normally used to identify the originating IP address of a user connecting to a web server through a load balancer or a proxy.
After playing around with this header, I found out, that TenX actually interprets the “X-Forwarded-For” header.
This means I was able to bypass the rate-limiting protection of TenX by using just one source IP.
I created a list of public source IPs and fed them into the Burp Intruder.
Again, some math:
Lets assume, that we are able to find the correct one time password after 500.000 tries within 30 minutes.
500.000/30/60 = 280 which means if we are able to test 280 combinations, we are able to bruteforce the PIN in about 30 minutes.
My internet connection at home is not the best one so I only managed around 70-100 requests per second.
I created a PoC video which demonstrates the whole account takeover attack:
But you actually came here to read about how to steal Bitcoins from TenX users, right? Well, go on then …
Maintaining Control Of The Pwnd Account
After a TenX user has signed into the account, the e-mail address as well as the phone number can be changed (at least via the web application of TenX). At this point I would assume some sort of validation like a confirmation e-mail to the old address.
Well, there is no such thing …
A confirmation e-mail is only sent to the new address but not to the old one. The same behavior occurs when changing the phone number.
This allows an attacker to completely lock out the victim out of his/her account and to maintain access to it after taking over the account.
Stealing BTCs and ETHs
The attacker has full control over the victims account. Even if the victim notices that his/her account was hacked, it would take hours to contact the TenX support and so on. Now, what about the funds of the victim? Even if there is some sort of verification e-mail before BTCs can be sent to another wallet address, it would not be a problem at all because the e-mail was already changed to an attacker controlled e-mail address.
But there are no verification e-mails. Not a single one of them …The attacker has full control over the victims account. Even if the victim notes that his/her account was hacked, it would take hours to contact the TenX support and so on. Now, what about the funds of the victim? Even if there is some sort of verification e-mail before BTCs can be sent to another wallet address, it would not be a problem at all because the e-mail was already changed to an attacker controlled e-mail address.
But there are no verification e-mails. Not a single one of them …
A TenX customer can just enter a destination wallet address, confirm the transaction by clicking a button on the web-application and that’s it. The victim wouldn’t even notice the theft …
I reported three different vulnerabilities:
- Remote Account Take Over Vulnerability
- Missing verification when changing e-mail address and/or phone number
- No additional security mechanisms when withdrawing funds
As of my knowledge, the last 2 vulnerabilities are still not patched at the time of writing. TenX merged all three vulnerabilities to one issue, paid me well and told me that I can publish a write-up.
Recommendations
I think the recommendations in order to patch those kinds of vulnerabilities are clear:
Never trust the X-Forwarded-For Header.
Do not rely on the source IP when it comes to rate-limiting – use something else like the username!
Add additional verification techniques when changing security critical information like the e-mail address and the phone number.
When a user changes the e-mail or the phone number, the user has to prove, that he/she has access to this e-mail/phone (to the old one!). This can be done by sending a confirmation link or a PIN to the old phone number / old e-mail address.
TenX should at least notify the user via the old email address, that those account details were changed.
- Add additional verification techniques when withdrawing coins.
TenX No Longer Supports The Webapp.
From here:
“Until March 12, 2018 (23:59 GMT), you’ll be able to continue using the web app to retrieve your funds. After that date, you’ll have to use an iPhone or Android phone to continue using TenX.”
It also seems, that changing the phone number is not possible through the mobile app.
Conclusion
I really like what TenX is doing and I think that they can revolutionize the way how BTC and other coins are used in our daily life.
But security is especially important when it comes to companies like TenX which work with BTC, ETH and other cryptos.
Stolen BTC funds are stolen – period. A victim can’t reverse a BTC transaction, that is simply not possible. This is why security needs a high priority – especially in companies like TenX.
TenX should fix the remaining issues ASAP but I also want to thank them for the good cooperation, for the nice communication with their bug bounty/security team and of course for the bounty.
Timeline
2017-11-26 - Reported 3 vulnerabilities to TenX via e-mail
2017-11-30 - Asked for updates
2017-12-11 - Issue(s) confirmed, $3000 payout in BTC
2018-01-23 - Confirmed that they patched the X-Forwarded-For issue and TenX gave me green light to publish this write up