15 Jan 2021
Insertion of Malicious Links for Execution in Profile Picture - Unvalidated User Input in MS SharePoint 2019 (CVE-2020-1456)
Today I am publishing a Finding discovered by my good friend user_x73x76x6E - have fun reading his writeup!
Although this vulnerability was not a typical JavaScript XSS, it was categorized as such by Microsoft. This write up should show that even if no script execution is possible, you can still attack users and infrastructure in other ways.
TL; DR
The SharePoint 2019 server for on-premises with implemented user profile options allowed for authenticated users to upload a profile picture. The path to an uploaded image in the users profile could be changed in the save dialog-request. Here, an arbitrary link could be inserted, allowing the user to attack everyone who visits a page with the user’s profile picture embedded. Because of the high occurrence of the profile picture in SharePoint, several attacks scenarios like DoS, user tracking, attack relaying and others are possible. This vulnerability was categorized as cross site scripting (XSS) and assigned the CVE ID CVE-2020-1456.
Setup
Windows Server
- Windows Server 2019 Evaluation
- Version: 1809
- OS build: 17763.379
- Windows Updates till 09/09/2019 12:13PM
- added Active Directory Domain Service
- promote Server to DC
- create new Forest
SQL Server
- Install MS SQL Server 2017 Evaluation Edition
- installation type: Basic
- Installer Version: 14.1805.40.72.1
- Database Version: 14.0.1000.169
- Install Microsoft SQL Server Management Studio Release 18.2
SharePoint 2019
- SharePoint Server 2019 (Setup Version 16.0.10337.12109)
- IMG file was saved as ISO with Passmark OSFMount (v3.0.1005.0)
- setup SharePoint as a Single-Server Farm
- add the User Profile Service Application.
Vulnerability Scoring
Vulnerability Class: Improper neutralization of user supplied input CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
CVSS 2
- Score 6.5 (Medium)
- Vector AV:N/AC:L/Au:S/C:P/I:P/A:P
CVSS 3.1
- Score: 6.5 (Medium)
- Vector: AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A
Detailed Description - Walkthrough
During a test of a SharePoint application I also partly tested SharePoint itself. In the SharePoint setup with user profiles enabled, each user could upload a profile picture. After uploading the picture, it could be reviewed in the user profile before finally accepting it and permanently save the changes, including all other entries.
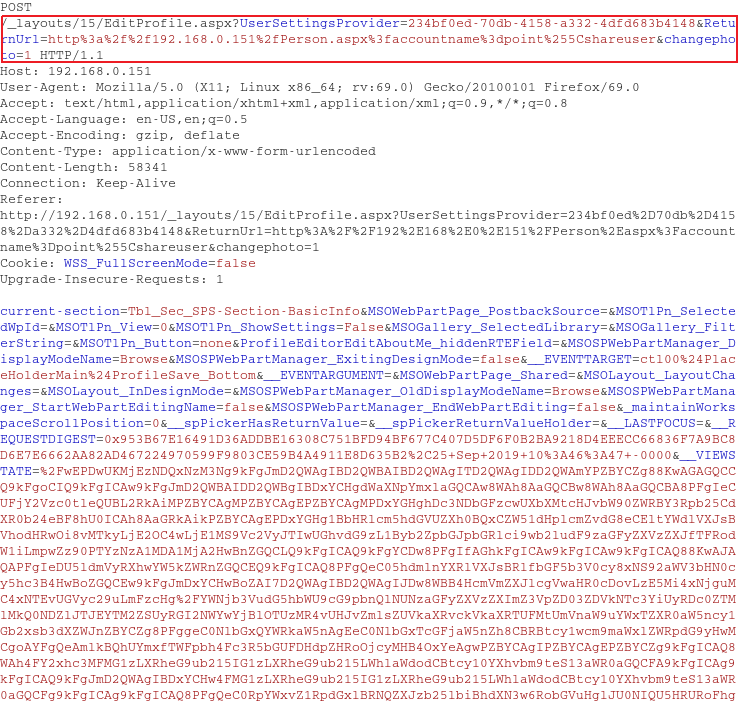
When saving all changes, the SharePoint performed a POST request, showing the changes for the user shareuser in the domain point as follows:
This request also contained the parameter ctl00$PlaceHolderMain$ProfileEditorEditPictureURL, which held the path to the uploaded profile picture as shown below in URL encoded form.
URL encoded Parameter and value
ctl00%24PlaceHolderMain%24ProfileEditorEditPictureURL=http%3A%2F
%2F192.168.0.151%3A80%2FUser%2520Photos%2FProfilbilder%2Fpoint_shareuser_Mthumb.jpg
Plain text parameter and value
ctl00$PlaceHolderMain$ProfileEditorEditPictureURL=
http://192.168.0.151:80/User%20Photos/Profilbilder/point_shareuser_Mthumb.jpg
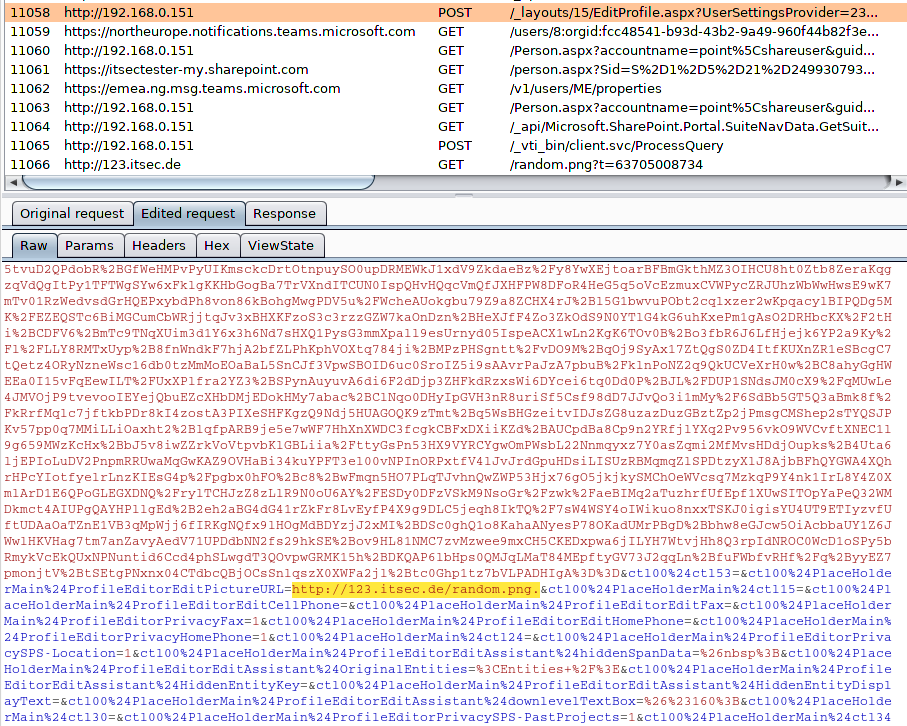
This POST request could be intercepted and the value of the parameter, changed to http://123.itsec.de/random.png. Because the server accepted the user provided input, the URL was embedded instead of the original URL to the locally stored picture.
Changed Parameter Value
ctl00$PlaceHolderMain$ProfileEditorEditPictureURL=http://123.itsec.de/random.png
The inserted URL was embedded instead of the profile picture. In this case, a 1GB “image file” was provided behind the link. As seen below, the “image file” was requested by the browser.
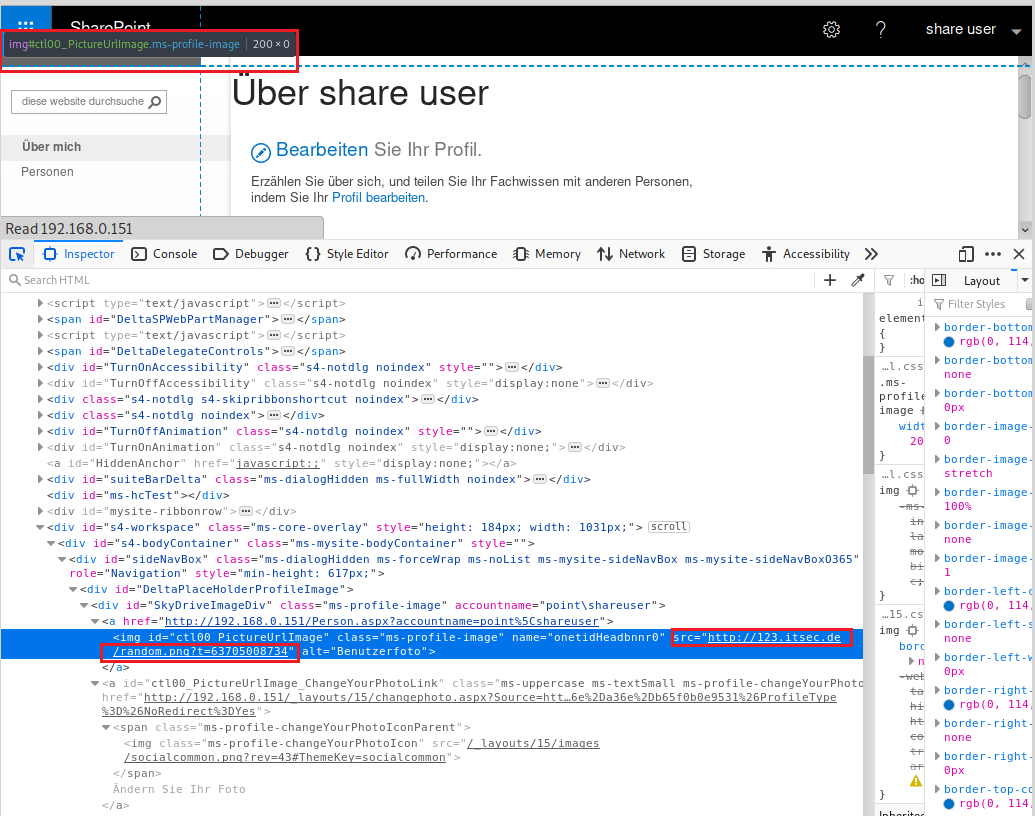
The embedded link could also be identified in the source code of the web page by analyzing the src parameter of the HTML img tag.
Conclusion
Every user who visits a site, where the corresponding user image is embedded, opens the link in the background. This allows for the user to be tracked, produce a lot of traffic in the network, being tricked to carry out prepared attacks and being flagged by internal and/or external systems because of suspicious or malicious behavior (trying to access blocked sites or similar).
Potential Damage and Attack Scenarios
There are several security implications for this kind of attack, especially when thinking of a larger company with many active users.
Denial of Service
The issue may be used to embed links to large files resulting in a Denial of Service (DoS) or a Distributed Denial of Service (DDoS). This can affect the local system because a large amount of data is downloaded with each request by the user. Alternatively, the whole company can be affected because multiply users are requesting a large amount of data, leading to a complete exhaustion of bandwidth or resulting in a Denial of Service at the firewall or company proxy.
This issue may also be used to perform crafted requests to resources on cloud infrastructure, leading to a ban of the companies IP address and thus to a Denial of Service for all other resources (e. g. websites) hosted at the same cloud provider.
Tracking (GDPR)
Because the default configuration of the IIS also sends a complete referrer, the embedded link may be used to track users and store all transmitted information, depending on the SharePoint application in use. This may lead to a breach according to GDPR regulations.
Internal path disclosure (default setting of IIS 10.0)
Because of the default configuration of the IIS web server, internal paths are also sent with each requests, improving the tracking and resulting into internal path disclosure.
Obfuscate attacks
Some attacks like Denial of Service, stored cross site scripting (XSS), cross site request forgery (CSRF) via GET and similar can be relayed by providing a link for other users to execute. If an attack link is embedded, each user visiting a site with the “profile picture” embedded, automatically performs the attack.
Reputation damage
The profile picture parameter can also be used to embed links to inappropriate or blocked sites, which are logged and/or blocked by company proxy. This may result into one or more employees being approached and possible given notice for inappropriate behavior.
Additional Thoughts
Because the impact would be even higher if all MS Office products would be affected, we also tested the Office 365 integration for the SharePoint on premise solution. However, even valid profile pictures in SharePoint on premise were not synced to Office365. If the pictures would be synced, there is a possibility that malicious links would be uploaded to all office products like Outlook, Teams, One Drive and SharePoint online.