17 May 2017
Google Bug Bounty - The 5k Error Page
Well, this is going to be quite a short post ..
In January I was looking at some Google services hoping to find something worth a bounty.
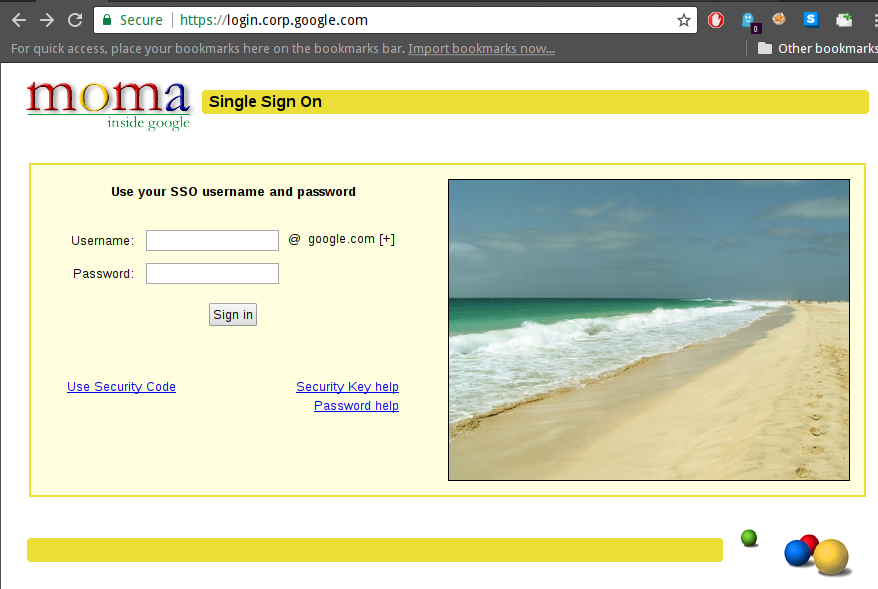
I came across https://login.corp.google.com which is nothing more than a simple login page (seems to be for Google employees themselves …)
Every time the page is accessed, a new image from https://static.corp.google.com is loaded directly into the page. Nothing too fancy happening here hm?!
An example of such an image URL is https://static.corp.google.com/corpsso/images/PICT0004.jpg
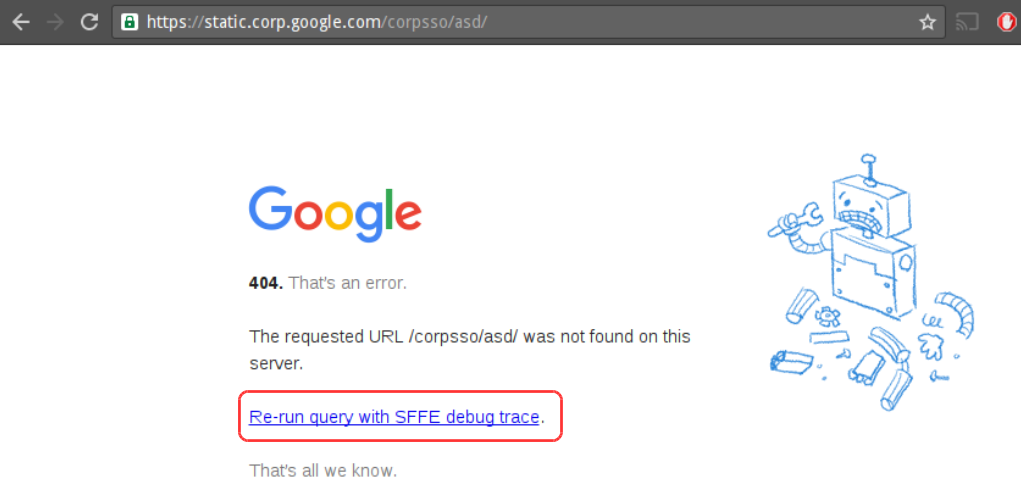
Well, after trying some other things I thought provoking an error here is the best thing I can do: I accessed https://static.corp.google.com/corpsso/asd/ and the default Google 404 page appeared with one difference:
I found a feature!
Lets check out what this is about. The “Re-run query with SFFE debug trace” link pointed to https://static.corp.google.com/corpsso/asd/?deb=trace.
Uff … That’s bad …
I was able to access internal debug information on static.corp.google.com by just adding “?deb=trace” to a 404 URL.
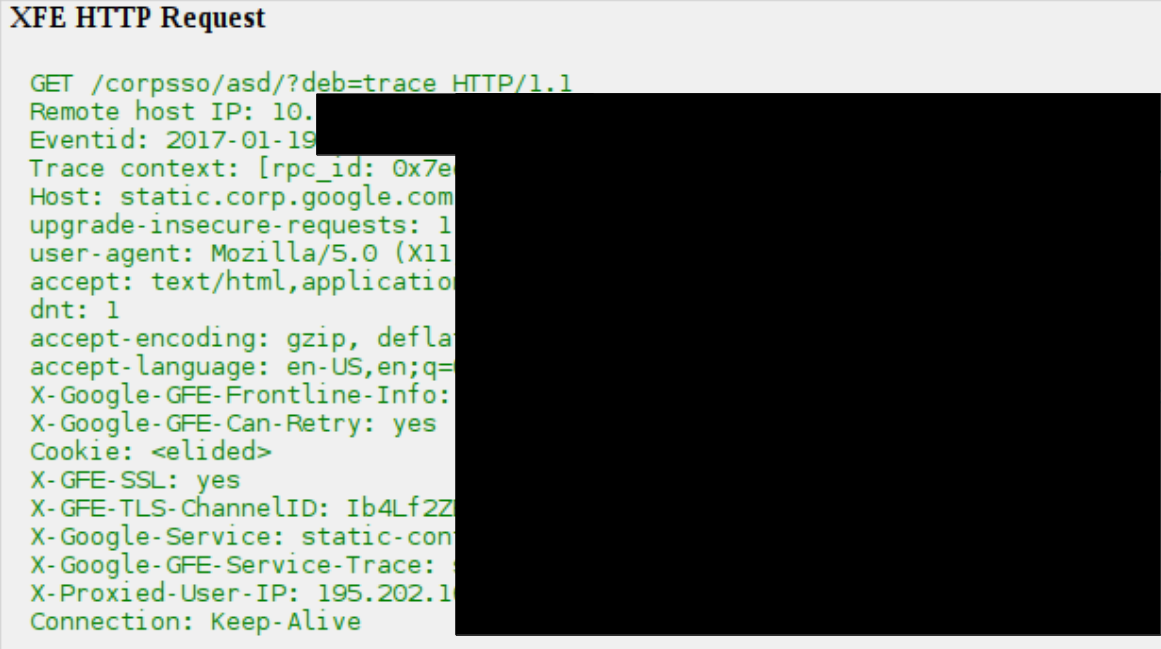
I saw the complete X-FrontEnd (XFE) debug trace and much more. I am still not sure what “SFFE” stands for but it seems that it’s something like a request engine in Googles backend that handles for example Bigtable Lookups.
Bigtable is a “high performance NoSQL database service for large analytical and operational workloads”. For more information go here.
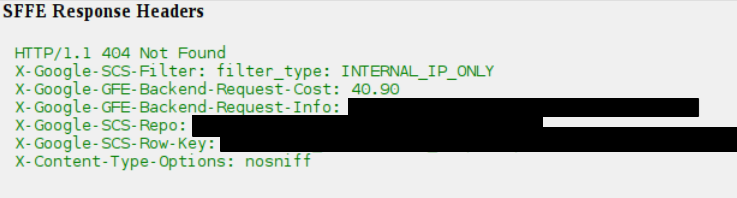
I was also able to view the SFFE response headers which indicate, that nothing was found …
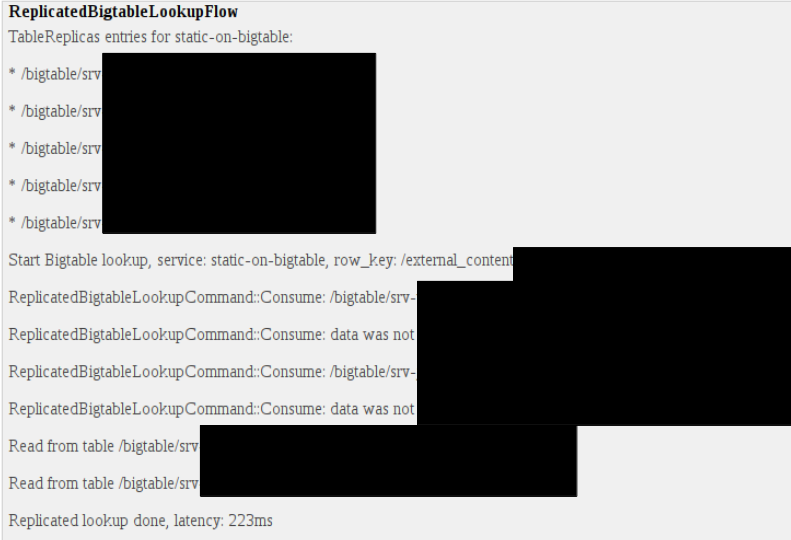
In another section of the debug page I had access the complete Bigtable lookup flow which was performed due to my request (sorry for all the blacking):
This flow contained table names and paths of different Bigtables which were queried because of my request. So basically I was able to access Google internal information like:
- Internal IP of the server which was used for the query (I think ..) + its uptime
- Name of the server (the name is actually a link which is not accessible from the Internet but seems to point to Google Borg clusters)
- SFFE Request and Response Headers
- XFE HTTP Request
- Replicated Bigtable Lookup Flow
- Service Policies
- …
The page did not allow any user interaction and I haven’t found anything to “go deeper” into the system so i reported it right away.
It was my first bounty I got from Google!
Detailed Reporting Timeline
19/01/2017 – Initial report
20/01/2017 – Report triaged
20/01/2017 – Nice catch!
10/02/2017 – Google already fixed the issue but forgot to tell me … I contacted them asking for an update
19/02/2017 – Got a response, they implemented a short-term fix and forgot to sent my report to the VRP panel …
10/03/2017 – Got $5000 bounty
16/03/2017 – Google implemented permanent fix