07 Nov 2016
Netflix Account Takeover through Automated Phone Calls
In the last few weeks I took a closer look on caller ID spoofing and the impact which this “feature” can have on todays online services. A few months ago I came across a great blogpost from Shubham Shah which is an Australian security researcher and pentester. You can find the post here.
He did great work 2 ½ years ago – he analyzed the impact of caller ID spoofing on 2 factor authentication on many popular services like Google, Facebook and so on. The caller ID is basically the number which gets displayed on the phone on the receiving end of the call. He was able to bypass the 2 factor authentication on this services quite effectively. For bypassing 2FA he used a long known issue which affects the authentication of voicemails - I will cover this topic in detail later on in this post.
Caller ID spoofing
But lets start at the beginning of the story:
Mobile network security is poor ….
We know that, that’s nothing new.
What many people do not know is, that the caller ID of everyone around the globe can be easily spoofed. Basically an attacker needs access to the phone network – which nowadays is very easy due to VOIP – and a provider which allows the attacker to set the caller ID as part of the configuration or allows the configuration of your own Private Branch Exchange (PBX) like Asterisk.
This blogpost for example explains, how to set up your own Asterisk server to spoof any caller ID you want. VOIP providers like voip.ms allow the user to set the outgoing caller ID directly within the web application – no additional software or hardware is required – not even a physical phone because a softphone (software which simulates a phone) can be used as well (e.g. x-lite).
An old and powerful Issue - Voicemail Hacking
Alright, so now that we know, that everyone with a computer and a credit card can spoof every phone number on the planet, what can an attacker do with this besides social engineering and prank calls?
Voicemails - It can be used to get access to the voicemail of everyone who is using a vulnerable telecom provider. There are still many mobile phone companies around the world which only use the incoming caller ID for authentication. No additional information is required from the user.
I did some research on Austrian mobile phone operators and I was really surprised. Basically I had a look at the “big three” mobile phone providers in Austria which are:
- A1
- DREI (Hutchison)
- T-Mobile
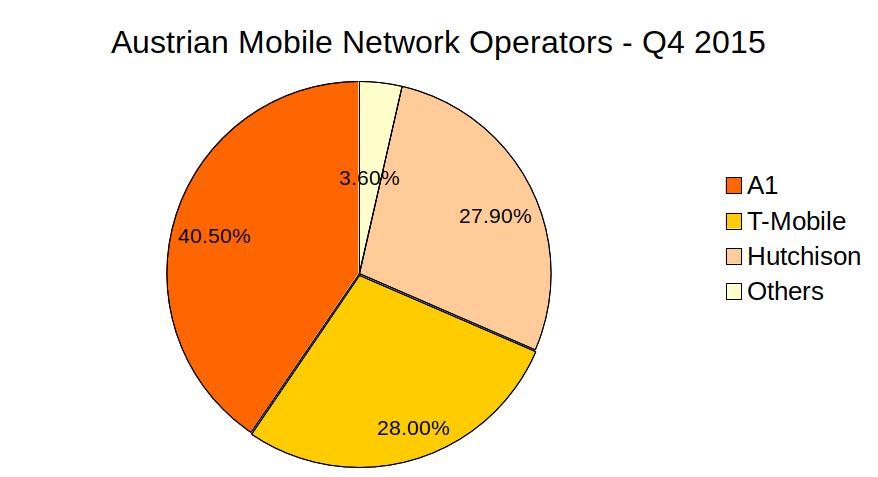
The following graph shows the detailed market share of those mobile network providers (Q4 2015).
The data for the graph above was taken from here (sorry, in German)
I checked those three main players including some of the companies which are using the same network and I got the following results:
- A1 – Not vulnerable to voicemail hacking
- Bob
- Yess
- DREI (Hutchison) – Not vulnerable to voicemail hacking
- T-Mobile - VULNERABLE to voicemail hacking
- Telering
- HOT
- S-Budget
According to the graph above, T-Mobile has a market share of 28% in Austria. Those are about 4 million users (according to T-Mobile). Remember, I have not tested every sub company of those three which are using the same network, which means that the number of affected users can be lower. But actually this means, that many Austrian T-Mobile users, which use the default configuration of their voicemail without password, are vulnerable to the voicemail hacking issue.
How can we use this as an attacker?
So, now we know that an attacker is (under certain circumstances) able to get into the voicemail of its victim but how can this be used to hack online services? Shubham Shah used this 2 ½ years ago to bypass 2FA of many services which are using automated phone calls to transmit the 2FA code. So when a user wanted to request the code, the user had the possibility to get an automated voice call which then told the code to the user. Due to the voicemail issue, it was possible to bypass this using the following exploit flow.
Exploit flow
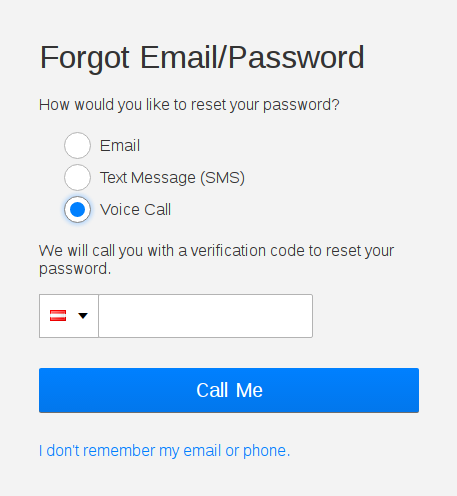
1.) Enter phone number of the victim
2.) Request voice call - At the same time, call the victim so that the automated call gets redirected to the
voicemail of the victim
3.) After some time, spoof the caller ID to get access to the victims mailbox
4.) Listen to the security code, which should now be on the voicemail
5.) Profit
What about Netflix?

At the beginning I told you, that this has something to do with Netflix … Well, Netflix had the same issue, but this time it did not affect the 2 factor authentication – it affected the password reset function …
This means, that if the victim added a phone number to his/her Netflix account to improve the security of the account, it actually weakened it. An attacker with the knowledge of the phone number of the victim (which uses a mobile network provider which is vulnerable to the voicemail issue) is able to reset the password of the victim. No interaction of the victim is required - One scenario would be, that the victim answers the call of the attacker – the Netflix phone call gets redirected to voicemail. The other scenario would be, that the victim does not answer the call at all – the Netflix call gets redirected to the voicemail as well.
I reported this to Netflix via the responsible disclosure program and I noticed, that they have a really good and fast responding security team – it took a little bit longer to fix the issue because the automated phone calls used by Netflix are handled by a third party. Beneath you can find a detailed reporting timeline.
Reporting Timeline
26/09/2016 – Initial report
28/09/2016 – Response (won’t fix)
28/09/2016 – Provided additional context due to the criticality of
the issue
04/10/2016 – Accepted the issue – rolling out a fix
04/11/2016 – Fixed
Mitigations
Basically, Shubham Shah already mentioned mitigations for this vulnerability in his post back then… But again:
Users should set a voicemail password (if the provider offers this feature – hopefully … )
Services, which offer automatic phone calls to transmit security codes or whatever should make sure, that the code is not spoken onto the mailbox. This can be achieved by adding some kind of user interaction in form of a key press before the security code gets transmitted. BTW, this is also how Netflix fixed the issue.
Final thoughts
I was surprised that T-Mobile is still vulnerable to this kind of issue. This is nothing new, it is no new discovery and everybody who is into security should be aware of this. I think, many people do not know that caller ID spoofing, SMS spoofing or E-Mail spoofing even exists and that it is relatively easy to do for everyone.
If you know mobile network providers which are vulnerable to the voicemail issue, let me know – contact details can be found here. If you want to discuss this issue or anything related to this – just reach out to me!
Update 2016-11-23
T-Mobile Austria resolved the voicemail-hacking issue for all their services except for “HOT”. According to the CISO of T-Mobile, they are not using the same systems as T-Mobile does.