29 Jun 2016
When Ebay implements a keylogging feature
Well, finally this is my first blogpost!
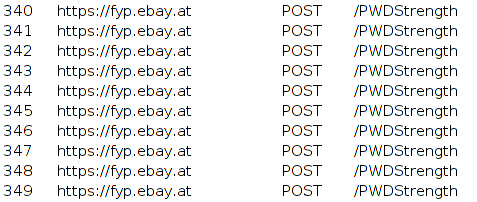
Recently I was looking a little bit into the Ebay bug bounty program. I had a look at the password reset function of Ebay and while typing in my new password, I was wondering, why the website is sending dozens of requests to Ebay’s servers.
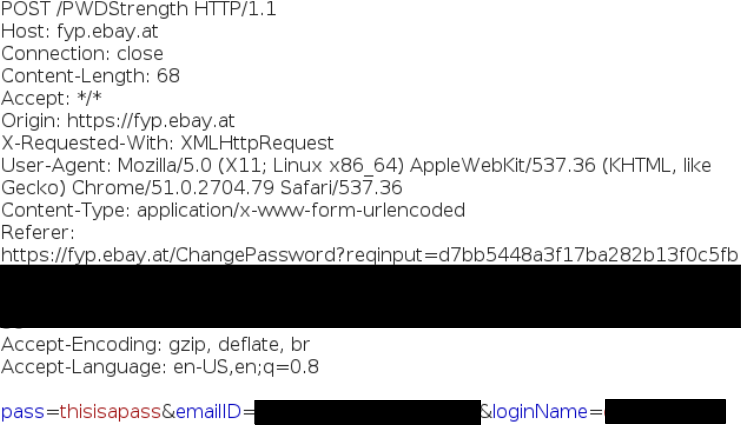
Actually, they are sending a POST request to /PWDStrength for every character a user is typing into the password box. Because this is not bad enough, they are adding the email-address and the username to the POST-body as well.
It seems, that they have implemented something like a “server-side password strength measurement tool” or whatever. It is common practice to enforce a password policy for web-applications:
Normally this is done on the client (via JavaScript) but it is also common to add server side checks to verify that the password is complex enough. But sending every character a user is typing into the password field, checking the complexity on the server and returning back “good” or “bad” is not the best idea, this is just a small key-logger. Imagine a user starts typing in the password which the user already uses for another service, but recognizes it before submitting it to Ebay’s servers. The user would expect, that no data is sent to the server as long as the new password was not set (submit button is pressed).
This is not a security vulnerability itself because I think they have implemented this for some reason. This is why I decided to report this to the Ebay security team because I wanted to know why they have implemented this in such a weird way.
Note When submitting a security vulnerability to Ebay, one can only do this via a HTTP-form … ¯\(ツ)/¯
Two days ago (27.06.2016) I got an answer from the Ebay security team:
Hello David,
Thanks for reaching out to us, but there are some reasons behind our current solutions but I wouldn’t be able to give you more details on it.
Thanks,
eBay Security Research
It seems, that Ebay does not want to share the secret behind this check. After receiving this email, I was wondering if Ebay checks the password in the same way when changing the password through the Ebay customer control panel. Well, yes they do, but not in the same way…
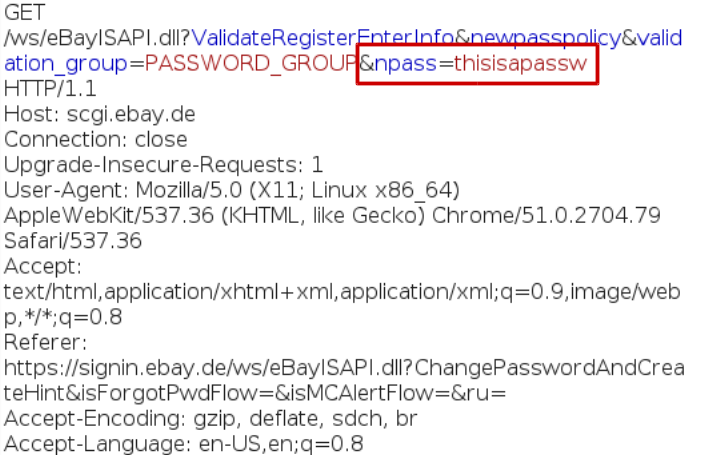
Instead of sending a POST request, they are using a GET request to send every key-press to Ebay’s servers.
This time the request does not include the username and/or the email-address, but they are using GET instead of POST. Parameters sent via GET can get cached by proxies and they appear in log-files. OWASP wrote about this issue as well: Sending data with GET method through HTTPS
Edit: Because there were some discussions just to be clear: The requests are all sent via HTTPS, this means that for example third-party proxies cannot see the URL or other parts of the HTTP headers or even the body. The main point I think is, that GET Requests are logged in log-files which are usually accessible by more people that the main database.
To sum this up
Checking the password completely on the server is OK, but sending every typed-in character to the server is not the right solution.
Sending sensitive information like passwords via GET is really bad practice. Like OWASP says “it is not a good practice to use the GET method to send sensitive data to a web application, because the information contained in the URL can be stored in many locations such as proxy and web server logs.”
Timeline
Tuesday, June 21, 2016: Reported Issue to Ebay security team
Monday, June 27, 2016: Got answer that they are not planning to do anything
For further questions and discussion, contact me with the provided details on this website.